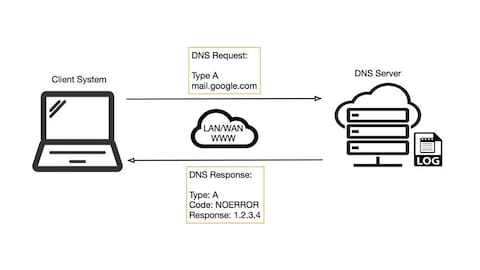
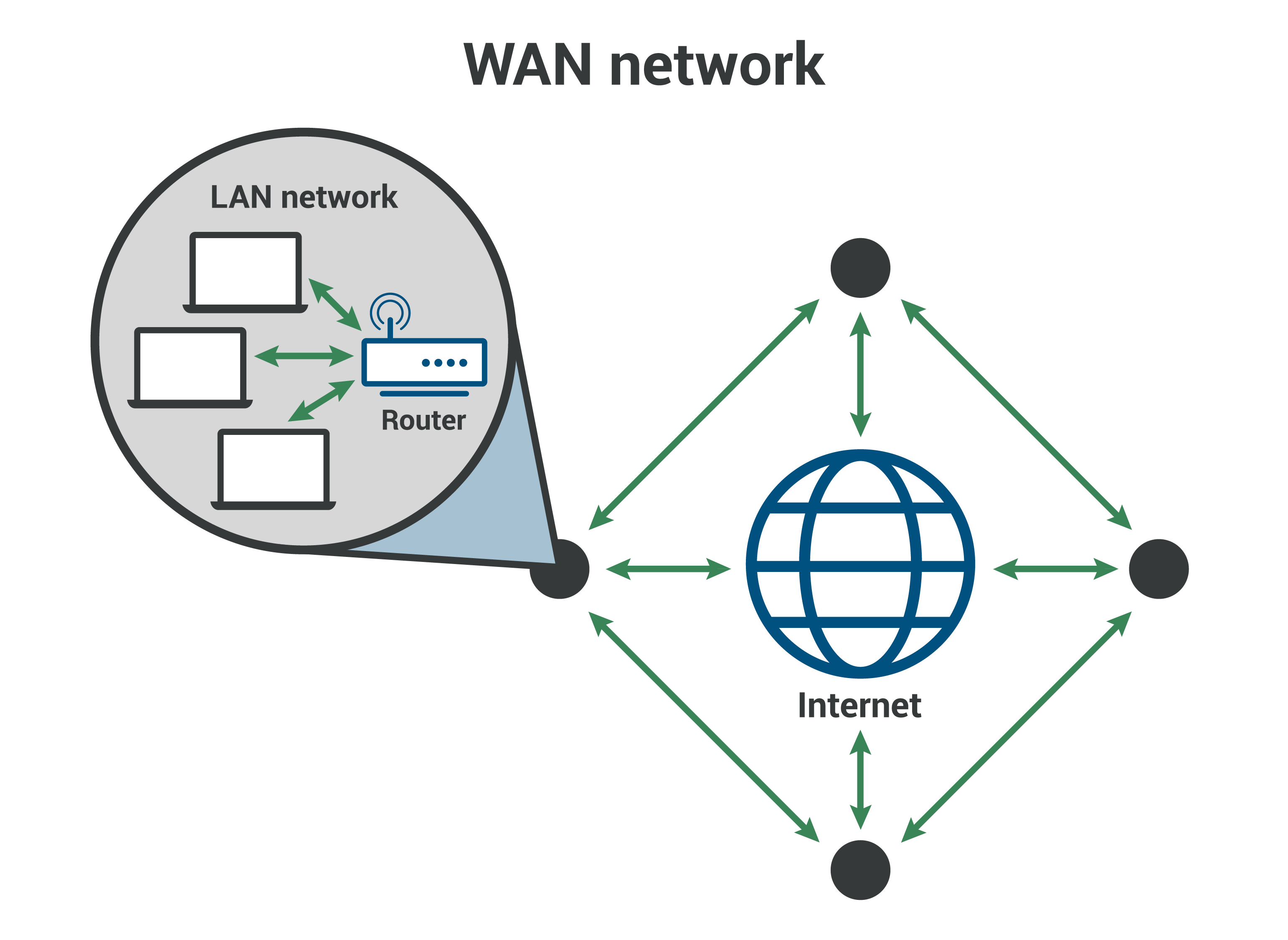
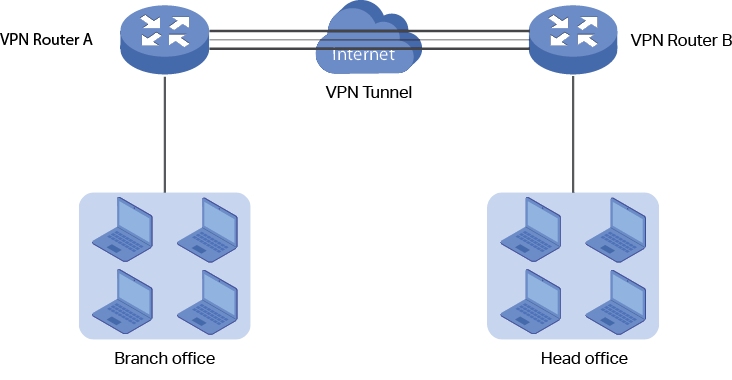
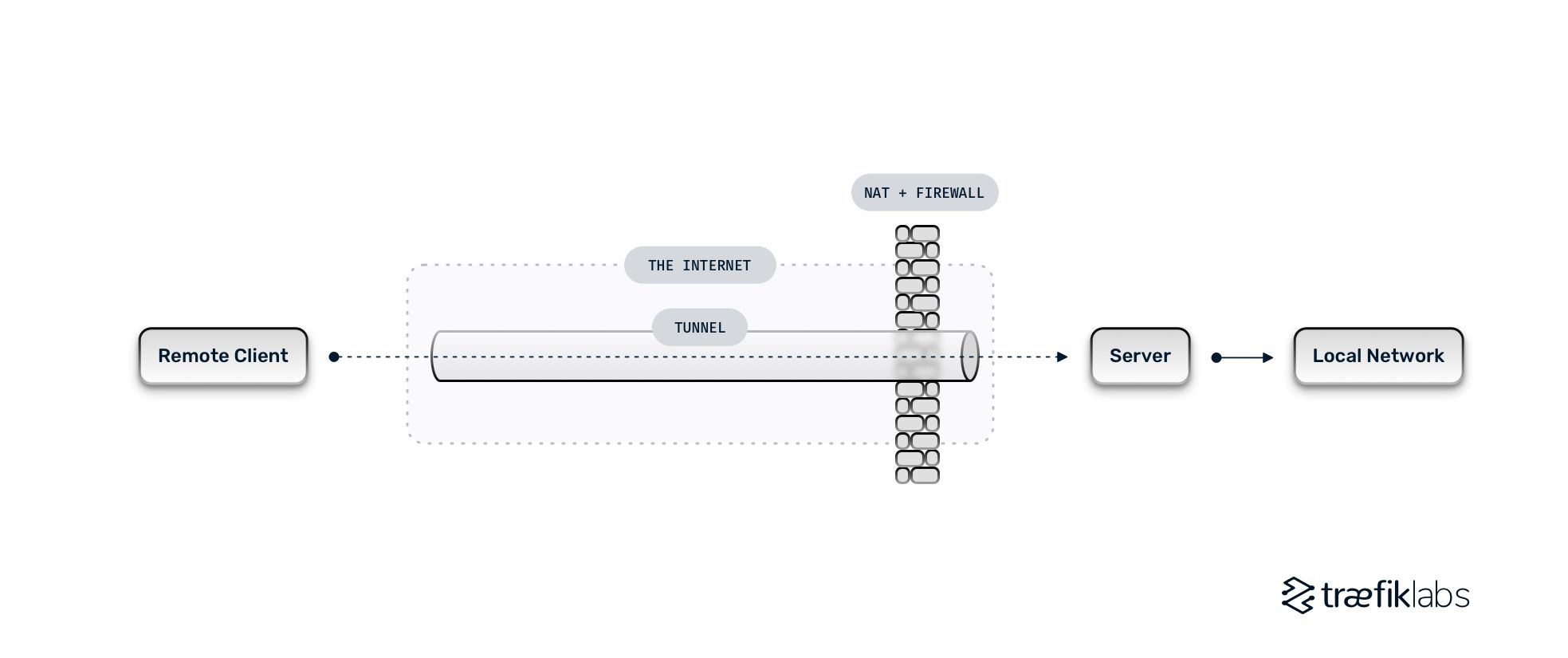
wifi - How do I set up a OpenVPN tunnel for Raspberry Pi on LAN without internet connectivity? - Raspberry Pi Stack Exchange

windows 7 - How can I tunnel from one computer on a Wi-Fi connection to another specific machine on the LAN? - Super User
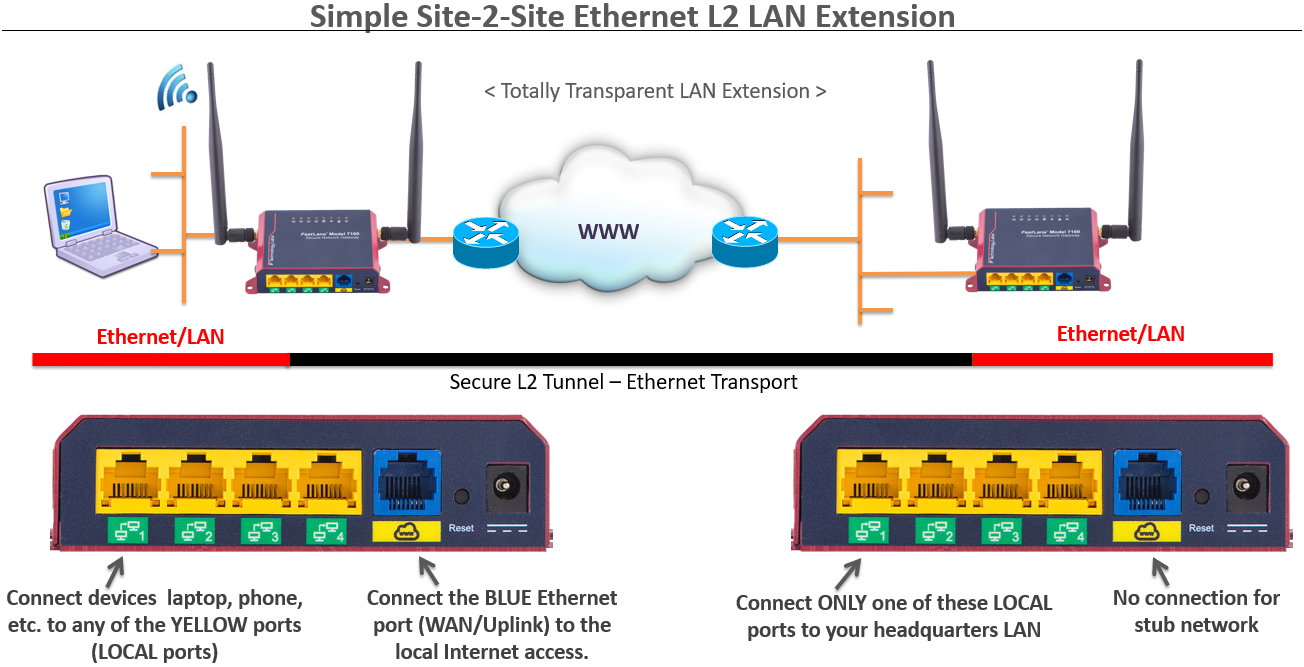
GoRemote™ Work-From-Home with Easy LAN Tunneling using the World's Longest Ethernet Cable - IP Technology Labs
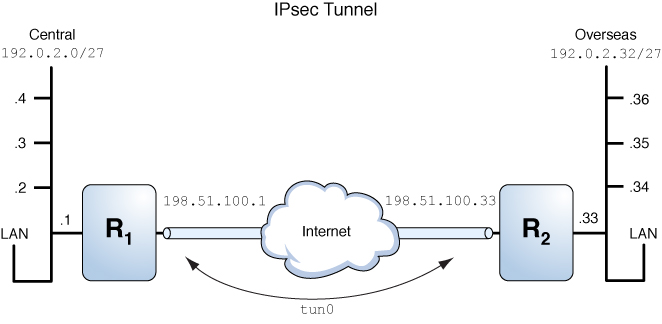
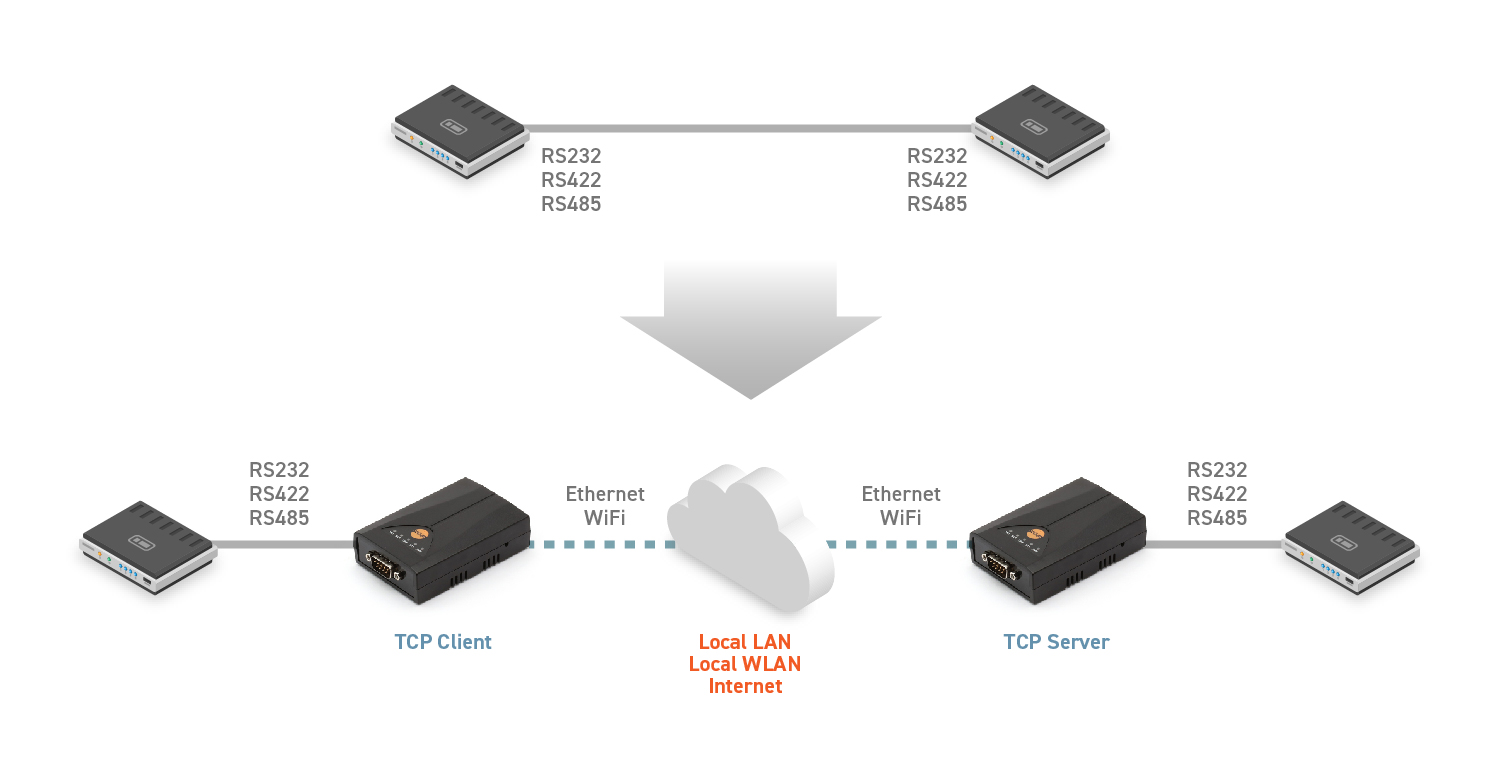

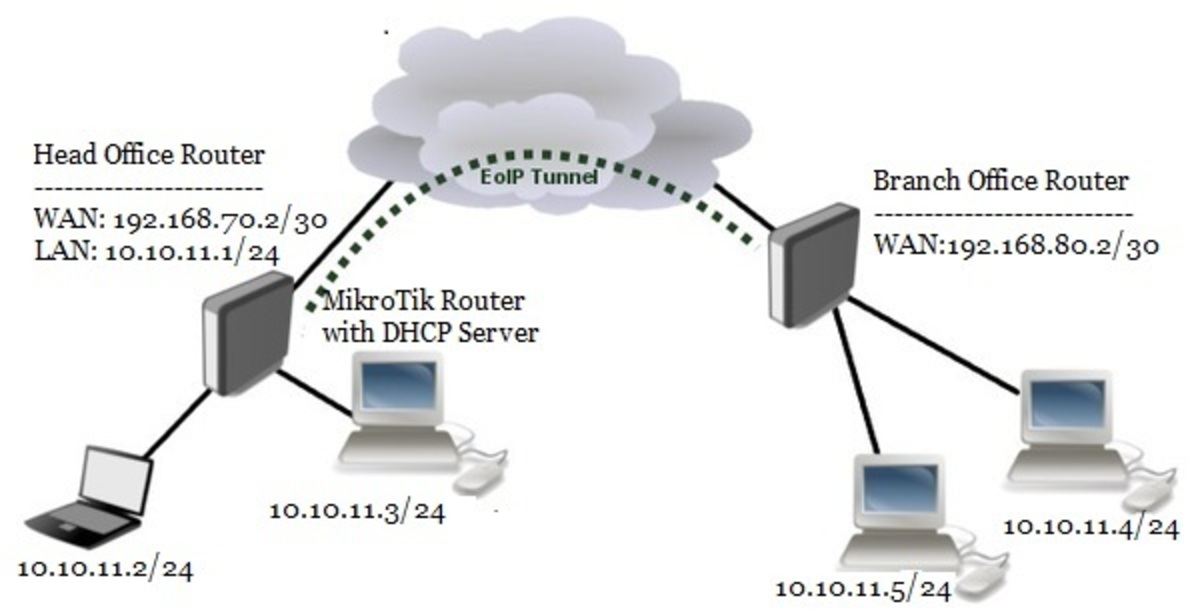

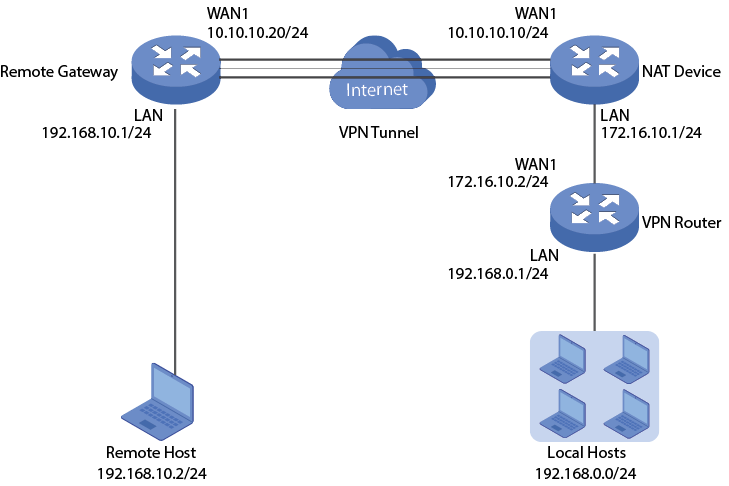

.png)