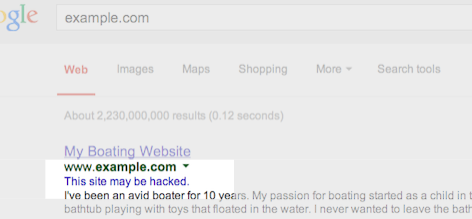
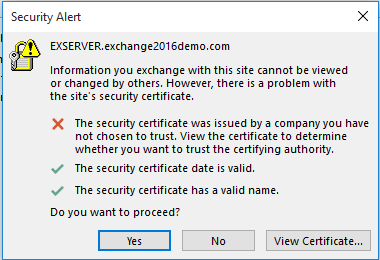
Chinese hackers who breached Google gained access to sensitive data, U.S. officials say - The Washington Post

Chargé d'Affaires, Nicholas J. Giacobbe, Jr. Remarks at the Hack to Learn and Protect Cybersecurity Conference - U.S. Embassy in Kosovo